Packet Analysis
Within your method of looking through the packets (using Wireshark), searching for the word flag- brought me directly to the flag.
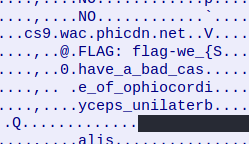
Using the “Follow UDP Stream” feature in Wireshark, you can see the whole flag inline.
txt 1 lines
Flag-we_have_a_bad_case_of_ophiocordyceps_unilateralis
Part 2 – Version 1
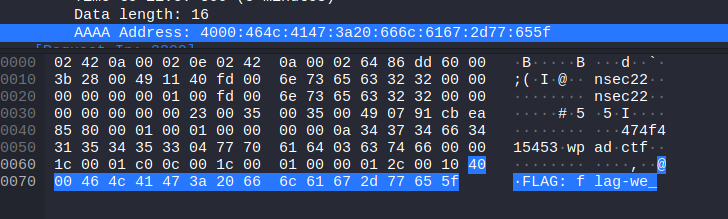
Farther down, the server returns commands:
ls –lacat wallet-priv.txt
The hex code is returned.
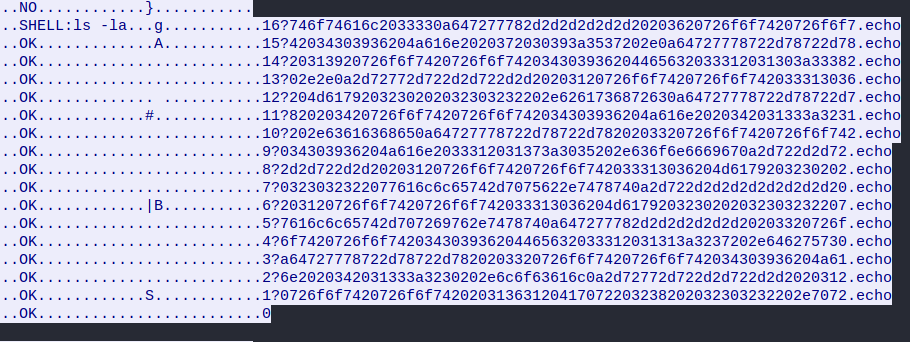
Part 2 – Version 2
Converted to text:
This is my method of finding this.
Narrowed down to host 23 to collect only these in tcpdump. I then cut out most of the before and after excess using:
bash 1 lines
tcpdump -nr portobello53.pcapng 'dst fd00:6e73:6563:3232::100 and src fd00:6e73:6563:3232::23' | cut -d " " -f 8- | cut -d "." -f -2 | cut -d "." -f 2- > hex.logThe command does the following:
tcpdump -nr portobello53.pcapngreads the packet capture file.'dst fd00:6e73:6563:3232::100 and src fd00:6e73:6563:3232::23'filters packets with the specified destination and source IP addresses.cut -d " " -f 8-extracts the relevant fields from the packet data.cut -d "." -f -2removes the domain suffix.cut -d "." -f 2-removes the first part of the domain, leaving only the hex code.> hex.logsaves the output to a file namedhex.log.
I used CyberChef, but after the excess is removed you can just type in Linux:
bash 1 lines
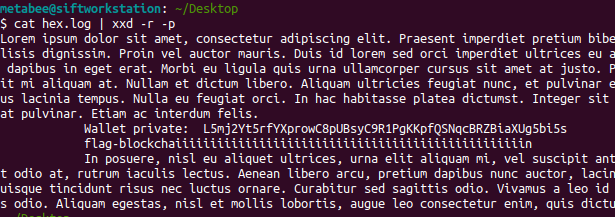
cat hex.log | xxd -r -p- This will convert the hex code back to text.
- You can also use CyberChef to convert the hex code to text.
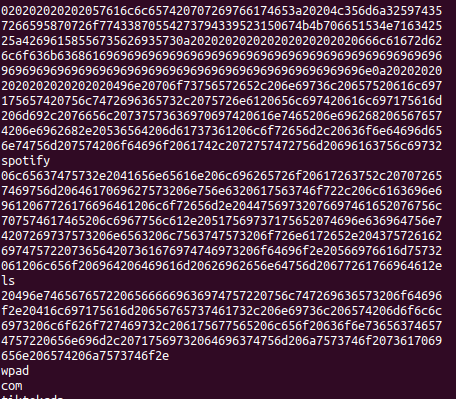
Last flag is:
txt 1 lines
flag-bargaining_{md5 hash of the string CVE-xxx-yyyy}Second Version