Description
Author: Venax
Jacky has learnt about the importance of strong passwords and made sure to encrypt the BitLocker drive with a very long and complex password. We managed to capture the RAM while this drive was opened however.
See if you can break through the encryption!
Solution - Using my Volatility Web Docker
I wanted to test my Volatility Web Docker setup for this challenge which had the dependency of lacking the bitlocker plugin. So thanks to lorelyai’s volatility3-bitlocker, I was able to integrate the necessary plugin and proceed with the analysis.
Setting up Volatility Web
With Docker, download and initial build the Volatility Web GUI Docker:
bash 3 lines
git clone https://github.com/JonesCKevin/Volatility3-WebGui-Docker.git
cd Volatility3-WebGui-Docker
docker compose up -d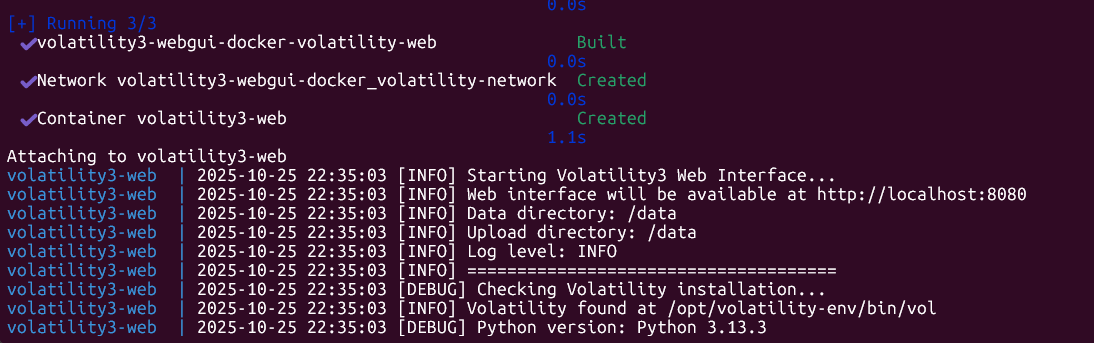
Once completed, move the memory dump provided into the
datadirectory.
Navigate to the webapp
Open your web browser and go to http://localhost:8080. You should see the Volatility Web GUI.
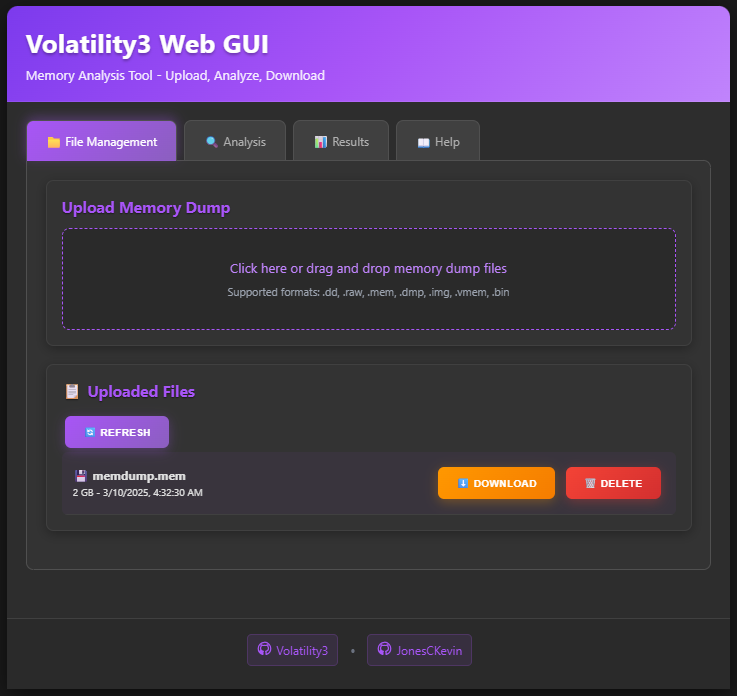
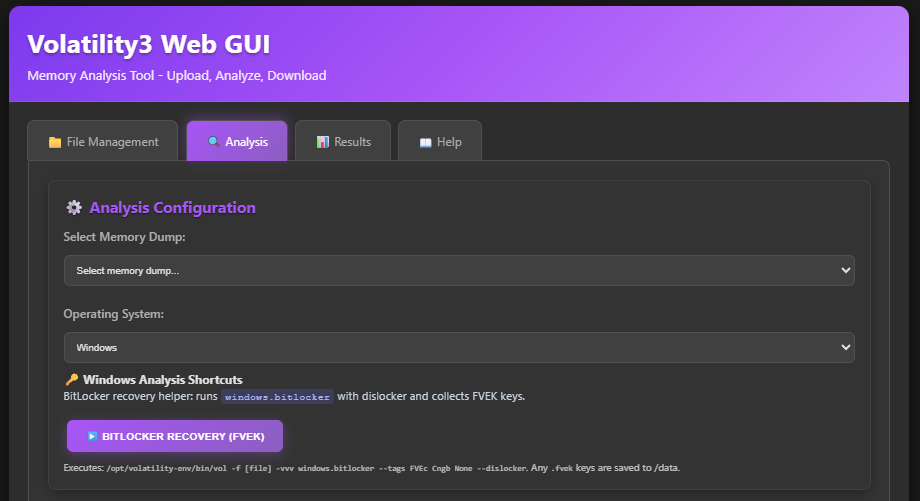
Initiate Analysis
Select Analysis tab and within the custom input type in bitlocker and press Run.
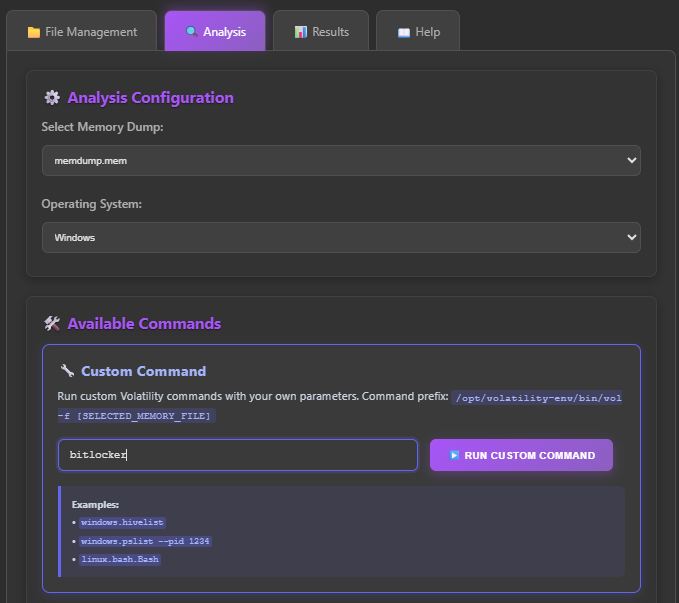
After an eternity and a half, the analysis completes and reveals the Bitlocker password.
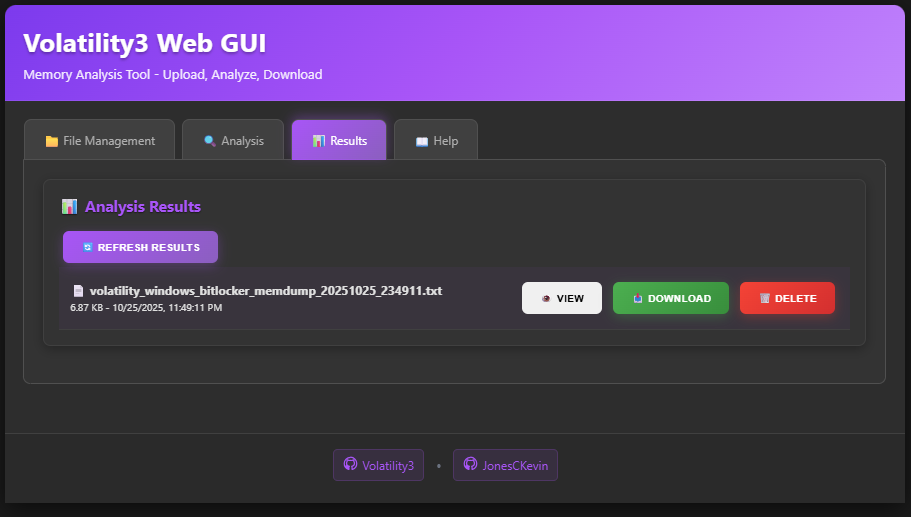
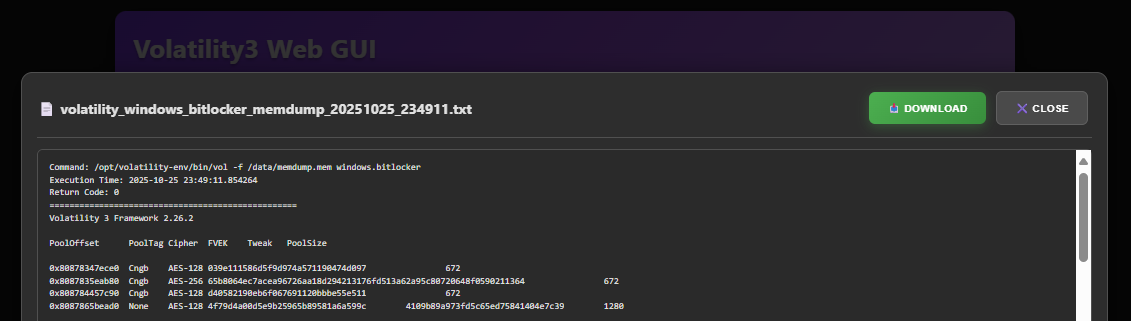
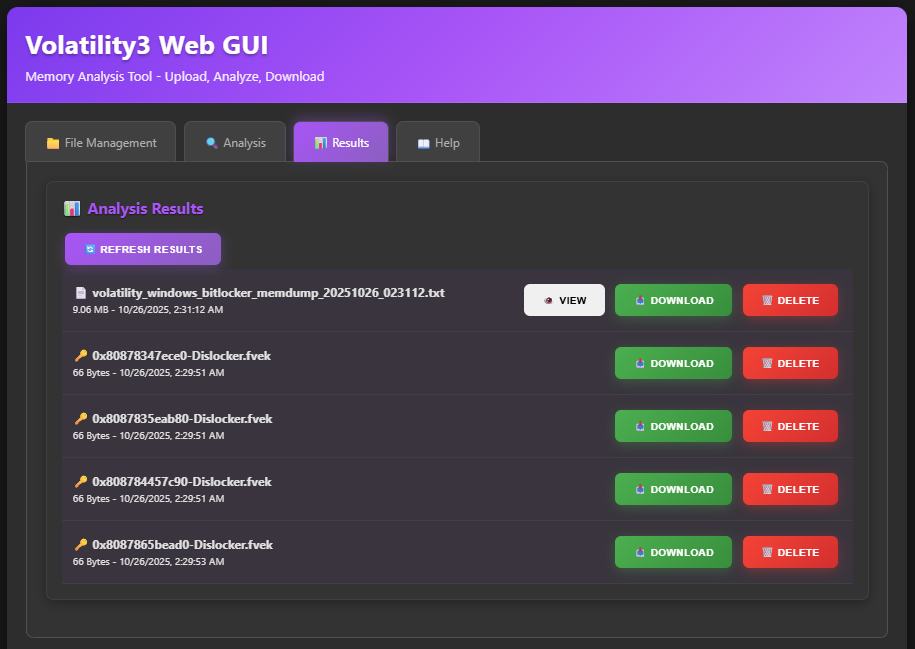
For transparency, I did end up running the command directly in the docker terminal to ensure it completed successfully using this specific command: This was because I needed the output files from the plugin to proceed. This should be added in the repo now.
bash 1 lines
/opt/volatility-env/bin/vol -f /data/memdump.mem -vvv windows.bitlocker --tags FVEc Cngb None --dislockerLinks will download the local hosted fvek file from my output
| File | Offset | Tag | Cipher | FVEK | Tweak | Size |
|---|---|---|---|---|---|---|
| File | 0x80878347ece0 | Cngb | AES-128 | 039e111586d5f9d974a571190474d097 | 672 | |
| File | 0x8087835eab80 | Cngb | AES-256 | 65b8064ec7acea96726aa18d294213176fd513a62a95c80720648f0590211364 | 672 | |
| File | 0x808784457c90 | Cngb | AES-128 | d40582190eb6f067691120bbbe55e511 | 672 | |
| File | 0x8087865bead0 | None | AES-128 | 4f79d4a00d5e9b25965b89581a6a599c | 4109b89a973fd5c65ed75841404e7c39 | 1280 |
Using the Password to Unlock the Drive
Make mount points
bash 2 lines
sudo mkdir /mnt/bit2-decrypted
sudo mkdir /mnt/bit2-fsUsing Dislocker to unlock the Bitlocker drive
bash 1 lines
sudo apt-get install dislocker ntfs-3gUnlock the Bitlocker volume
bash 1 lines
sudo dislocker -v -k 0x8087865bead0-Dislocker.fvek -V bitlocker-2.dd /mnt/bit2-decryptedMount the decrypted filesystem
bash 1 lines
sudo mount -t ntfs-3g /mnt/bit2-decrypted/dislocker-file /mnt/bit2-fsPlain Text 4 lines
The disk contains an unclean file system (0, 0).
Metadata kept in Windows cache, refused to mount.
Falling back to read-only mount because the NTFS partition is in an unsafe state. Please resume and shutdown Windows fully (no hibernation or fast restarting.)
Could not mount read-write, trying read-onlyAccess the mounted filesystem and retrieve the flag
bash 5 lines
ls /mnt/bit2-fs
# '$RECYCLE.BIN' 'System Volume Information' flag.txt
cat /mnt/bit2-fs/flag.txt
# picoCTF{}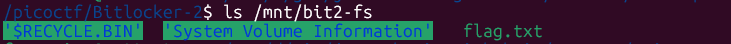
Clean up mount points
bash 4 lines
sudo umount /mnt/bit2-fs
sudo umount /mnt/bit2-decrypted
sudo rmdir /mnt/bit2-fs
sudo rmdir /mnt/bit2-decryptedUpdate for Web UI
Flag Answer
Click to reveal the flag
Full: picoCTF{B1tl0ck3r_dr1v3_d3crypt3d_9029ae5b}
Resources
- Volatility Web Docker: Github - JonesCKevin
- Volatility3: Github - volatilityfoundation/volatility3
- Volatility3 Bitlocker Plugin: Github - Lorelei